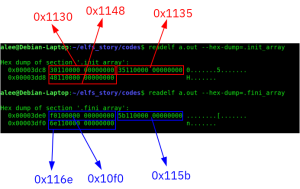
In the upcoming part of our discussion, I will delve into the intricacies of ELF Sections. These sections serve as containers of critical information required for linking a target object file to produce a fully functional executable. Each section plays a key role in the overall structure and functionality of the executable file.
ELF’s Story Part3: ELF’s Structure: ELF Section Headers
1-Introduction Are you ready to delve deeper into the world of ELF files? In my previous part, I discussed the critical role of the ELF header in locating different parts of the file. Today, I want to share with you some exciting information about the ELF Section Headers. These headers serve as descriptors for various […]
ELF’s Story Part2: ELF’s Structure: ELF Header
1-Introduction In the previous part of this story, we learned about compilation, linking, and how a linker works. In this part, I would like to discuss the ELF (Executable and Linkable Format) structure and the elements that make up an ELF file. An ELF file is not just a binary code that executes on a […]
CVE-2023-38831: WinRAR Bug Or Windows Feature? In-Depth Analysis of Winrar CVE-2023-38831 Vulnerability
winrar CVE-2023-38831 vulnerability: Hi again,In the recent week, we saw that a new vulnerability was published by Group-IB from Winrar.I decided to analyze it in detail and find out why this type of vulnerability which is very very simple, should occur in such essential software like Winrar.At first look, I thought that this vulnerability was […]
ELF’s Story Part1: How is an ELF create
1- Introduction Hello guys I’m back with a new series of blog posts.Last year I focused on Linux binaries. I read a lot about ELF files, How they compile, and how load in memory and run. So I decided to write my experiences in some blog posts and named it ELF’s story. But this is […]
Flareon2020-Level10
break Assets: First Section: Static Analysis This challenge is a very hard one. You have a Linux ELF file that uses many anti-debugging techniques that don’t let you debug and analyze it easily.The file is x86 ELF and when you run it, shows you a prompt to enter a password.OK, when you open it in […]
Flareon2020-Level9
9-crackstaller Assets: First section: The hard challenges starts at the moment. This file is a executable file that at the first glance, we see the .data section is encrypted. So we have a file that probably is packed. Ok let’s run it in a VM to observe its behavior. I use a Windows7-x64 as guest […]
Flareon2020-Level8
8-ttt2 Assets: This is special challenge which is uses the new feature of Windows 10, WSL. The WSL is an embedded Linux OS in the windows that lets you to run the Linux files in it. For more info read this OK at first, I run the ttt2.exe file and it shows me an error […]
Flareon-2020-Level7
7-re_crowd Assets: First Section: This challenge is just a PCAP file. At the first place open it in the Wireshark, we see some HTTP GET requests and responses. For extracting the content of that webpage, Open it in the NetworkMiner software to extract the content of this pcap file. To import the dump to NetworkMiner, […]
Flareon-2020-Level6
6-codeit Assets: At first glance it is a UPX packed exe file. Unpack it with UPX and we see that file doesn’t run.This is a trick for Anti-unpacking. The malware author used some Hardcoded address in the malware code which if you unpack the malware, the unpacked version overwrites those addresses, and the unpacked malware […]
Flareon2020-Level4
4-report Assets: First Section: This is a VisualBasic Macro that stored in a Excel file.When opening the VBS script in VisaulBasic, I see it has a form(F) which stores two long string values in a textbox and a label object. Also the script has a Sheet1 file that in it, is the code of the […]
Flareon-2020-Level3
3-Wednesday Assets: This is a score game and you must get a specific score at this game so that it shows you the flag.After debugging the code, I saw that strings Score and High Score in the screen of game. Searched them in the memory of the file and find the address of them. I […]
Flareon-2020-Level2
2-garbage Assets: First Section: When we run the exe file, we see an error message from windows, that this file is invalid or something else.When we open file in a hex-editor, at the end of file we see that the Manifestxml which windows uses to run the program, is corrupted.The file is packed with UPX. […]
Flareon2020-Level1
1-Fidler Assets: First Part: This is very simple. When you run the fidler.exe file, it shows a password box. The password checker function is simple. copy the password_check() in a new file run it with Python and print the ‘key’ value: “ghost”. def password_check(input): altered_key = ‘hiptu’ key = ”.join([chr(ord(x) – 1) for x in […]
Flareon7-2020
This year I started the Flareon2020 challenge a week late but I could finish it.The number of challenges was less than last year, but was harder. I ranked 359 in the scoreboard in this year. not bad 😀 .I wrote a short and simple of my write-ups for the challenges in this repo. Also I […]